
In today’s digital environment, keeping patient data safe is more than just a legal necessity or a matter of HIPAA compliance. It has now become the second most important aspect of reliable healthcare services, right after effective care outcomes.
The Health Insurance Portability and Accountability Act (HIPAA) sets two standards to safeguard Protected Health Information (PHI) under its Security and Privacy rules. When health care facilities, practitioners or their vendors fail to comply with HIPAA standards and regulations it becomes a HIPAA violation. These violations have serious implications like fines, damage to reputation and loss of patient trust. Knowing what constitutes a breach is the first step in being HIPAA compliant.
HIPAA Privacy Rule Violations
The HIPAA Privacy Rule outlines the conditions under which PHI can be accessed, stored, managed or disclosed. It also throws light on who must be given access to PHI based on their role and responsibilities. Privacy Rule violations are most commonly the result of ignorance or oversight, but carry serious consequences either way.
Improper disclosures: This includes whispering to a coworker about a patient’s condition, especially in public spaces, or sharing protected health information with family members who do not have the authorization to receive it. For example, a nurse speaking about a patient’s cancer diagnosis in a hallway might inadvertently provide information to those within earshot.
Accessing records without need-to-know: Browsing through a celebrity’s medical records or trying to find out about a neighbour’s health condition without their authorization is a direct violation of the HIPAA Privacy Rule. Unless you are a healthcare staff member who is directly involved in providing care to the patient, accessing this information, even if not for any malicious intent, is punishable by law.
Over-disclosure of PHI: This refers to releasing too much patient information to insurers, employers or business associates. For example, when asked to confirm a patient’s status of insurance coverage for a particular ailment, the designated healthcare staff member must ensure that they do not divulge any additional information about the patient’s treatment unless they are required to do so by law.
Unauthorized use of information: A fitting example for this type of HIPAA violation is the use of PHI for marketing or research purposes without written approval from the patient. Even well-meaning applications, such as sharing stories for a community newsletter, or promoting a new service to existing patients, can be considered violations when no consent is obtained. Those might seem small acts, but they do erode patient trust and can subject your clinic to fines.
HIPAA Security Rule Violations
The HIPAA Security Rule covers the various physical, technical and administrative safeguards that must be put in place to protect electronic PHI (ePHI). As more healthcare-related services move to digital platforms, protection of ePHI has become even more crucial in ensuring ongoing HIPAA compliance.
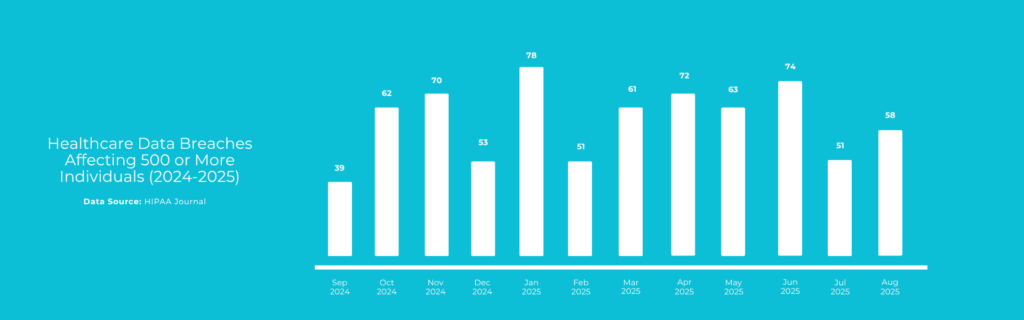
Weak technical measures: Such as deploying obsolete firewalls or weak passwords, or failing to encrypt sensitive information, are among the most common Security Rule violations. Healthcare systems are a frequent focus of hackers because PHI is so valuable on the black market. For example, the 2025 Healthcare Data Breaches report found that in August 2025 alone, 58 healthcare data breaches (each affecting 500 or more individuals) were reported to the Office for Civil Rights (OCR), exposing the protected health information of 3.79 million people through misconfigurations, unauthorized access, or other technical failures.
Data Source: HIPAA Journal
Lost or stolen devices: This category of violation involves the loss or theft of unencrypted devices such as laptops, USB drives, and smartphones that contain PHI. To avoid such violations, not only must employers train their staff to handle such devices with utmost care and in a manner that is compliant with HIPAA Security Rules, but they must also ensure that the data stored in such devices is encrypted at all times.
Improper disposal: Despite strict adherence to HIPAA rules during PHI storage and disclosure, a healthcare organization or business entity can still leave their organization vulnerable to HIPAA violation charges if they do not properly dispose PHI. Discarding printed medical records or hard drives in the garbage rather than shredding or securely wiping them is an example of improper disposal. There have been multiple cases in the past where such oversights have been discovered by dumpster divers.
Insufficient access control: When an organization fails to limit PHI access to only those members of the staff who need the information to carry out effective healthcare services, it becomes classified as a Security Rule violation. Implementing role-based access control is the only way to avoid such violations. For instance, a billing clerk does not need access to lab results.
Shared passwords: Allowing multiple members of the staff login to PHI platforms and CRMs using the same credentials is also a HIPAA violation. While many organizations allow this practice in good faith, this makes it impossible to track who accessed what information, leaving the organizations exposed during audits.
Administrative Failures that are HIPAA Violations
Ensuring HIPAA compliance is not just about employing secure technology solutions. It involves setting up efficient processes, strong governance and strict oversight. Administrative failures are a leading cause of compliance breakdowns.
No Risk Assessments: Conducting regular risk assessments is important for organizations to stay on top of their security gaps and process inefficiencies. Without documented assessments, it can be impossible to prove proactive compliance.
No policies & training: A large number of HIPAA privacy breaches take place every year simply because staff members are unaware of the existence of certain rules. Without regular HIPAA compliance training, healthcare staff may not fully understand their roles, and responsibilities. Hence conducting HIPAA compliance training and setting up breach prevention polcies are important HIPAA compliance measures.
Failure to appoint privacy/security officers: HIPAA rules state that someone must always be in charge of privacy and PHI. Things get dropped through the cracks when roles aren’t assigned and accountability is lost.
No Business Associate Agreements: Another serious administrative oversight that is considered a HIPAA violation is the absence of a Business Associate Agreement (BAA) when working with third-party vendors and service providers. Business associates like billing firms, IT consultants or cloud-based software providers must sign paperwork affirming that they understand their HIPAA responsibilities. Not doing so puts both the covered entity and vendor at risk.
Breach Notification Failures that are HIPAA Violations
The HIPAA Breach Notification Rule clearly requires healthcare organizations and business entities to notify patients in the event that their protected health information gets compromised during a security breach incident. Failure to comply with the breach notification rules, including delayed notification can attract fines from the OCR.
Delaying notifications beyond the 60-days limit set by HIPAA, failing to notify the right individuals, skipping reports to the OCR and/or the media are examples of HIPAA violations that come under the Breach Notification rule.
State & Federal Overlaps
HIPAA is federal, but many states have additional privacy requirements. Some of the providers are bound by state privacy standards, too. For example, California’s CCPA gives consumers more control and access to personal data when compared to HIPAA. Washington’s My Health My Data Act expands the (narrowly defined) term health data and tightens regulatory compliance.
When state and federal laws overlap, a violation of HIPAA can also be in breach of state statutes and may result in additional penalties.
Best Practices to Avoid HIPAA Violations
Preventing violations takes thoughtful planning and an ongoing culture of compliance. Healthcare leaders should make it a practice to conduct regular risk assessments, document findings, apply fixes and monitor progress. They must also invest in providing continuous HIPAA compliance training. HIPAA training must not be a one-time event, and must be made compulsory for staff to take refresher courses every year so that they are updated on the latest modifications to HIPAA rules.
Using HIPAA-compliant communications channels also go a long way in ensuring a safe and protected healthcare environment that builds patient trust. From using secure email platforms, data encryption, to maintaining audit logs and role-based accesses, healthcare organizations must integrate compliance into day-to-day work.
The cost of HIPAA violations is more than compliance failure; they also jeopardize patient safety and tarnish the reputation of healthcare organizations. From privacy rule violations like improper disclosures to security lapses such as weak passwords, every failure carries real-world consequences. Fortunately, with consistent risk assessments, strong technical safeguards, and ongoing HIPAA compliance training, organizations can prevent violations and build a culture of trust.
Frequently Asked Questions (FAQs)
- What is considered a HIPAA violation?
When a healthcare organization or business partner fails to comply with HIPAA rules and ends up creating an environment that does not fully protect PHI from external threat, it is considered a HIPAA violation. This could involve unauthorized disclosures, lack of safeguards, failure to notify patients of breaches, etc.
- Can employees be held personally liable for HIPAA violations?
Yes, employees can face disciplinary action, termination, or even criminal charges depending on the severity of the violation.
- What is the most common type of HIPAA violation?
The most common violations include unauthorized access to PHI, improper disclosures, lack of encryption, and insufficient staff training.