
When the Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996, the goal was to create a framework that would help protect sensitive patient health information (PHI) from being misused by healthcare organizations, insurance providers and allied healthcare service providers. Over the years, HIPAA has dramatically improved the baseline level of PHI security in the United States with the help of the Office for Civil Rights (OCR), which constantly monitors for HIPAA violations and levies heavy penalties for HIPAA breaches by employers.
In this article, we will take a closer look at the 10 most common types of HIPAA violations, both intentional and unintentional, real-world examples of HIPAA violations by employers over the last two decades, and steps that can be taken to prevent them from happening at your healthcare clinic or business.
What is HIPAA Violation
Before we begin, let’s understand how the OCR and the Department of Health and Human Services (HHS) define a HIPAA violation.
A HIPAA violation is any action (or inaction) that puts a patient’s protected health information at risk or fails to comply with the HIPAA privacy, security, or breach reporting standards.
It occurs when a covered entity or its business associate fails to comply with any of the HIPAA rules. The organization responsible for the violation is charged with HIPAA breach penalties depending on the impact and nature of the breach.
Why HIPAA Violations Still Happen in 2025
Since its enforcement in 1996, the OCR has received over 300,000 complaints of HIPAA rule violations and has collected more than $165 million in penalties and settlements. Over the years, healthcare organizations and businesses have become more aware and sensitised to the proper ways of handling patient health information. Needless to say, HIPAA has definitely improved the healthcare data protection and management practices in the US.
But despite these improvements, breaches continue to happen, especially with the advent of digitization and the rise of cyberattacks. According to the HHS, the OCR reported 588 healthcare data breaches in 2024 alone, impacting nearly 180 million individuals.
The cost of these breaches continues to rise, with IBM’s 2024 Cost of a Data Breach report revealing that healthcare has held the highest data breach costs across all industries since 2011, averaging a staggering $10.93 million per incident.
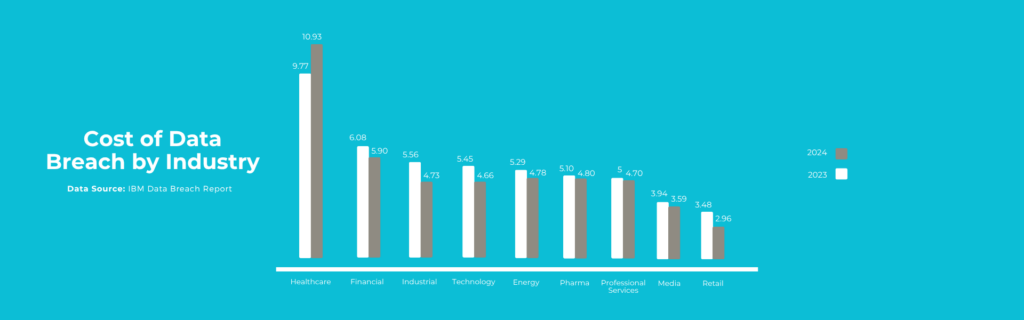
Image source: IBM
The IBM report and other statistics point towards the need for increasing awareness among covered entities and business associates as to what constitutes a HIPAA violation and its significance and impact, so that they may take the necessary steps to prevent them and avoid heavy HIPAA breach penalties.
Below, we list the 10 most common HIPAA Violations in the US and discuss some real-world cases associated with each.
HIPAA Violation #1 – Unauthorized Access to PHI
The most common type of HIPAA violation reported is the unauthorized access of PHI by employees at healthcare facilities. This happens either when an authorized employee is given access to more patient data than what is necessary to offer the required service, or when PHI access is given to employees who are not directly involved in the care service.
While the former is a clear violation of the HIPAA Privacy Rule’s Minimum Necessary Standard, the latter violates both the HIPAA Privacy and Security Rules.
One of the most famous examples of this HIPAA violation is the Cedars-Sinai Medical Centre breach of 2013. The hospital fired six of its employees for inappropriately snooping into medical records of celebrity patients, including Kim Kardashian, and faced a $95,000 HIPAA fine.
In this particular case, the nature of the HIPAA violation by the employees was intentional. However, the hospital was responsible for ensuring that PHI access was given only to staff members directly involved in the case, and that physical and technical safeguards were in place to protect unauthorized access.
How to Prevent
Here’s how hospitals can prevent unauthorized access to PHI and avoid such HIPAA violations.
- Implement role-based access control that clearly identifies employees with authorization and PHI data management at each role.
- Maintain audit logs and enable system monitoring to closely track employee activities and logins.
- Conduct HIPAA Compliance training for employees on the “minimum necessary rule.”
HIPAA Violation #2 – Lack of Risk Analysis and Assessment
After unauthorized PHI access, the next most common type of HIPAA violation reported is the failure to conduct regular risk assessments. The HIPAA Security Rule mandates that all covered entities perform risk analysis and audits on a regular basis to identify any lapses or gaps in security or privacy. However, most healthcare organizations and businesses often overlook this procedure until, of course, a breach happens.
In February 2024, a data breach at the Montefiore Medical Center impacted over 12,000 patients. An investigation by the OCR revealed failure to conduct risk analysis and lack of adequate security procedures as reasons for the breach. This violation cost the hospital a fine of $4.75 million in addition to the loss of patient trust.
How to Prevent
All covered entities and business associates must strictly perform risk analysis and assessments on a regular basis. It is also a good idea to conduct external security audits. At the end of these assessments, healthcare organizations must also act on rectifying identified gaps in security. For more information, refer to the HHS Risk Analysis Guidance document.
HIPAA Violation #3 – Mishandling of PHI Disposal
HIPAA Compliance does not end at PHI collection, storage, and management. Proper deletion of patient information or disposal of devices that hold it is equally important. Despite strict HIPAA regulations, many clinics, hospitals, and business associates still underestimate the risks associated with mishandling physical records and electronic devices that contain sensitive patient data.
When documents, unencrypted hard drives, laptops and mobile devices, or medical labels are discarded improperly, organizations risk unauthorized access of PHI such as Social Security numbers, diagnosis codes, and insurance details that can be misused. This is a clear violation of the HIPAA Security Rule – Physical and Technical safeguards.
An example of this HIPAA violation is the New England Dermatology and Laser Center (NEDLC) incident of 2021. The Massachusetts-based practice had been disposing “specimen containers with an attached label that contained PHI as regular waste, bagged and placed in an exterior dumpster accessible via the parking lot, without alteration to the PHI containing label,” the OCR stated, imposing a HIPAA fine of $300,640.
How to Prevent
Here are some steps to ensure that your healthcare organization does not violate the PHI disposal provisions within HIPAA.
- Ensure all physical documents containing PHI, like lab reports, patient charts, and medical labels are shredded before disposing.
- All old hard drives containing PHI must be securely wiped before disposing.
- It is best to use HIPAA-certified disposal vendors
- Conduct HIPAA Compliance training for staff on proper PHI disposal and policies.
HIPAA Violation #4 – Lost or Stolen Devices Without Encryption
Unencrypted mobile devices, laptops, or USB drives pose significant risks under HIPAA rules. Encryption of technology that handles PHI is mandatory for HIPAA compliance, and failure to do so makes it a violation of the HIPAA Security Rule. When lost or stolen, these unencrypted devices can leave PHI susceptible to misuse.
In 2021, CardioNet, a cardiac monitoring service provider, faced a $2.5 million penalty after an employee’s unencrypted laptop containing the PHI of over 1,300 patients was stolen from a parked car. The wireless health service provider did not have any policies for securing their mobile devices’ physical protection, and did not have any encryption implemented to secure ePHI.
How to Prevent
Strict adherence to the HIPAA Security Rule is the only way to prevent such violations. According to the Rule’s Physical Safeguards,
- All devices that contain PHI and ePHI must be secured and encrypted
- Covered entities and businesses must have remote access wiping tools that allow for the secure disposal of ePHI
- Mobile device management (MDM) systems are recommended for organizations that rely heavily on mobile devices for care services
- Employees must be trained on the importance of keeping devices safe
HIPAA Violation #5 – Failure to Enter Business Associate Agreements (BAAs)
A Business Associate Agreement (BAA) is a legally required contract between a covered entity and a business associate. As a third party that handles PHI on behalf of the covered entity, business associates like billing companies, cloud service providers, etc, must not handle PHI or ePHI without a properly executed BAA signed by both parties.
Unfortunately, this clause under the HIPAA Privacy Rule is often overlooked, either due to ignorance or lack of knowledge on vendor qualification procedures. This type of HIPAA violation can have a huge impact on patient data security and can attract huge fines from the OCR.
Without a valid BAA, the covered entities, like hospitals and clinics become completely liable for any HIPAA violation caused by the vendor. The Raleigh Orthopaedic Clinic breach incident is an example of the case in point.
The North Carolina-based healthcare provider had disclosed x-rays and associated PHI of 17,300 patients to an organization that was hired to digitize the images, without entering a BAA. This act led to a data breach in 2013, which was investigated by the OCR and cost the clinic $750,000 in HIPAA settlement.
How to Prevent
When dealing with business associates, healthcare providers, and other covered entities must ensure the following to stay compliant and steer clear of such violations.
- Ensure all vendors with access to PHI sign a BAA
- Maintain an updated vendor risk register
- Conduct vendor due diligence and audits
Read more about the HHS provisions for BAA here.
HIPAA Violation #6 – Inadequate Employee Training
Any organization or business that handles PHI is not fully compliant with HIPAA until all of its employees have a proper understanding of HIPAA rules and regulations. Covered entities and business associates that do not train their employees on the proper ways of collecting, handling, managing, storing, and disposing PHI and ePHI, risk increased likelihood of data breaches. Even the most advanced security systems can’t protect PHI if the people using them aren’t trained to do so.
Lack of employee training is often cited as a root cause in enforcement actions. Employees without proper HIPAA Compliance training are more likely to click on phishing links, mishandle printed records, lose unencrypted devices, or share PHI through unsecured channels.
How to Prevent
Healthcare organizations and businesses need to conduct regular HIPAA Compliance training for their employees. These training sessions must be made mandatory while onboarding new employees. They must also encourage existing employees to take refresher courses on an annual basis so that they stay updated on the latest HIPAA rules and regulations.
In order to make these trainings effective, organizations can,
- Customize training based on employee roles and responsibilities.
- Maintain detailed training records that include dates, modules completed, and quiz results. These can be used during audits or OCR investigations to demonstrate compliance.
HIPAA Violation #7 – Delay in HIPAA Breach Notification
According to the HIPAA Breach Notification Rule, failure to notify the OCR or the HHS about a breach within the stipulated time is a HIPAA violation on its own. This category of violation is more common than one would expect, and happens both intentionally (to cover the breach incident) and unintentionally (due to lack of knowledge about notification timelines or magnitude of breach impact).
Under the rule, covered entities and business associates are legally required to notify affected individuals, the HHS, and in some cases the media within 60 days of discovering a breach involving unsecured PHI. This OCR penalises this violation aggressively because not only does it constitute a non-compliance, but it also delays necessary actions that could mitigate harm for patients affected by the breach.
In February 2024, Change Healthcare, a subsidiary of UnitedHealth Group, suffered a massive ransomware attack that compromised a vast amount of patient data, reportedly impacting one-third of the US population. While the breach occurred in February, notifications to affected individuals didn’t begin until late July, well past the 60-day deadline mandated by HIPAA.
This delay sparked widespread criticism and concern, as it may have prevented patients from taking timely protective measures such as identity theft monitoring or securing their financial accounts.
How to Prevent
Failure to report a breach promptly is often caused by a lack of preparedness or unclear internal protocols, or even a lack of understanding of reporting timelines. Here’s how organizations can avoid this common misstep:
- Establish a clear breach response policy and protocols that outline breach identification, accountability, and communication channels for escalations.
- Conduct HIPAA breach response and notification training to compliance officers and IT staff.
- Use HIPAA-compliant incident management tools that detect and log potential breaches in real time.
HIPAA Violation #8 – Sharing PHI via Unsecured Communication Channels
Using unsecured communication channels to share ePHI is a very common yet easily preventable HIPAA violation. This violation includes using personal email accounts, SMS/text messages, or unencrypted messaging platforms like WhatsApp or standard email clients to send sensitive patient data.
This act is in direct violation of the HIPAA Security Rule, which mandates the use of protected and encrypted communication channels for sharing ePHI.
An example of such a violation is the American Medical Technologies (AMT) Data Breach of 2019. The AMT data breach impacted over 47,000 patients and exposed data including their names, medical record numbers, Social Security numbers, diagnosis information, health insurance policy numbers, and other personal identifiers.
Upon investigation, it was revealed that the supplier of medical supplies had been using an unsecured email, lacking proper encryption or access control to share PHI. This incident served as a reminder of the importance of using HIPAA-compliant email service providers for healthcare.
How to Prevent
Securing communication channels should be a top priority for any organization handling PHI. Here’s how to proactively prevent this type of HIPAA breach:
- Implement HIPAA-compliant communication tools such as Brightsquid Secure Mail.
- Ensure that patient portals are encrypted
- Block or restrict access to personal email accounts on work devices.
- Disable auto-forwarding of emails that may contain PHI.
- Educate employees on what constitutes ePHI and why standard email/texting tools are not secure.
- Provide step-by-step guidance on how to use secure messaging tools.
HIPAA Violation #9 – No Patient Authorization for Disclosure
Another frequently overlooked HIPAA violation is the disclosure of PHI without written consent from the patient. Covered entities and business associates must ensure that they obtain a written consent from patients before disclosing PHI, unless the disclosure is specifically permitted or required under HIPAA (such as for treatment, payment, or healthcare operations).
A violation under the HIPAA Privacy Rule, such disclosures can undo years of reputation building and attract heavy fines from the HHS.
An example of such a violation can be found under the HHS case files, where an “HMO impermissibly disclosed a member’s entire medical record to a disability insurance company without obtaining a valid authorization. The OCR investigation revealed that the form used was not compliant with the HIPAA Privacy Rule.”
How to Prevent
To remain compliant and protect patient privacy, healthcare organizations must treat consent documentation and authorization forms with the same level of care as clinical records. Here’s what you can do to stay clear of such violations.
- Always obtain appropriate written authorization for non-treatment disclosures.
- Use digital consent management tools that provide time-stamped consent logging and are easy to track and retrieve
- Train staff on HIPAA-compliant release forms
HIPAA Violation #10 – Poor Physical Safeguards
In a world where everything is being digitized and cloud-sourced, maintaining proper physical safeguards for PHI can sometimes be overlooked. However, this is an important part of the HIPAA Security Rule.
For instance, healthcare organizations must ensure that charts, files, computers, and other sources of PHI are not visible, accessible, or vulnerable to unauthorized individuals in physical environments, such as waiting rooms, administrative offices, or shared workspaces.
A HIPAA violation occurs when organizations fail to restrict physical access to sensitive data, increasing the risk of theft, loss, or accidental disclosure.
In one of the largest HIPAA settlements to date, Advocate Health Care Network experienced a significant data breach affecting approximately 4 million patients when their unencrypted desktop computers were stolen. The largest health system in Illinois had to make a massive $5.55 million settlement with the HHS, along with mandatory corrective actions.
The OCR investigation revealed that Advocate failed to implement appropriate physical safeguards to protect patient information. Specifically, the organization did not adequately limit physical access to the workstations, nor did it ensure the devices were secured with encryption.
How to Prevent
Covered entities and business associates must implement physical safeguards to ensure that their PHI remains secure. Here are some practices that might help:
- Secure workstation layouts
- Use privacy screens on monitors
- Use electronic access systems to restrict entry to file storage rooms, server closets, administrative offices, etc.
Jeff MacKay
Jeff MacKay, Director of Marketing at Brightsquid, is an optimizer with 20+ years of doing, learning, and leading in communications and advanced business technology implementation. For nearly a decade, he has focused on operational efficiency in healthcare, helping thousands of organizations implement more effective processes while also supporting enhanced privacy compliance. A true collaborator, Jeff pushes teams to challenge the status quo, rolling up his sleeves to help implement the resulting innovations. Jeff is a regular conference speaker, student of practical privacy compliance, cybersecurity trends, and technology in healthcare.